String Encryption
Protects sensitive strings with strong algorithms to prevent exposure of keys, passwords, or API tokens.
Develop, integrate, and secure your applications with Rika .NET Obfuscator. Enjoy powerful obfuscation techniques like code virtualization, anti‑tamper, string encryption and more for your C# and .NET software.
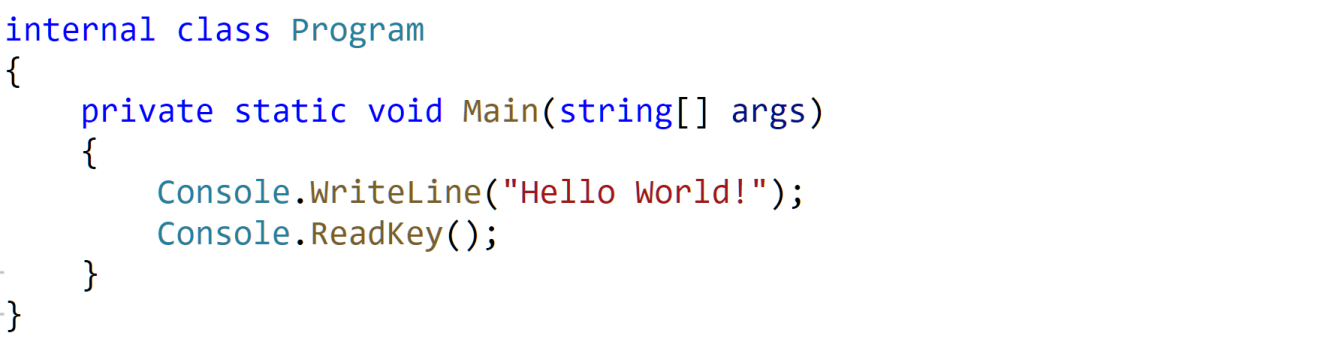
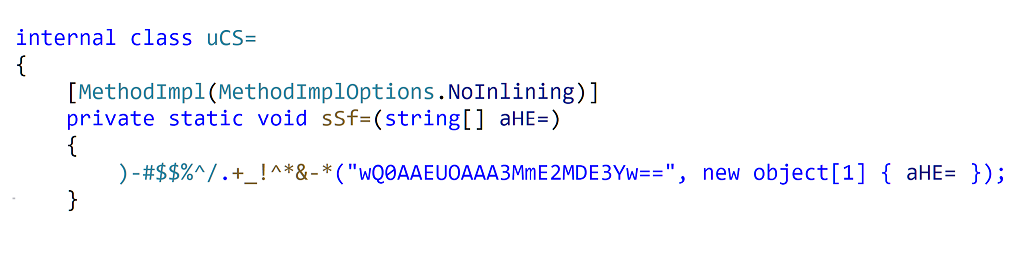
Designed specifically to make reverse-engineering harder.
Protects sensitive strings with strong algorithms to prevent exposure of keys, passwords, or API tokens.
Transforms methods into a unique virtual machine (VM) format.
Prevents static decompilers from viewing your original code and blocks tampering attempts.
Obfuscates classes, methods, and many other identifiers into meaningless names.
Modifies structure to unreadable forms without changing logic.
Encrypts embedded resources to prevent direct access by external tools.
Replaces direct reference calls with indirect proxy calls.
Detects virtualized/sandboxed environments and terminates execution if detected.
Preserves public member names for referenced libraries to avoid breaking functionality.
| Platform | Supported Versions |
|---|---|
| .NET Framework | 2.0 – 4.8.1 |
| .NET Core / .NET | 1.0 – 11.0 |
| .NET Standard | 1.0 – 2.1 |
Fully supported for all obfuscated assemblies.
Compatible with .NET Core and .NET 5+.
Note: Rika .NET has limitations. .
Yearly
$129.99
Not Included
Yearly
$259.99
Python obfuscator for advanced protection
Secure Auth with Rika.NET integration
Yearly
$599.99
$150/user
One subscription per team member
One subscription per team member
"The best obfuscator ever! The tool is incredibly strong, easy to use, and the obfuscation process takes very little time to complete."
"The virtualization is better than any other public virtualization."
"Really great obfuscator and code virtualization, I used to use Eazfuscator before Rika .NET, but it started to get really bad and my software got unpacked, but now I decided to switch to Rika .NET and it didn't disappoint."
Removing, bypassing, or altering watermarks, signatures, or protections is strictly prohibited.
Using the obfuscator with malware, RATs, or harmful software is strictly prohibited. If your file is reported as malicious, your license will be immediately revoked.
Reverse engineering, decompiling, or disassembling the obfuscator itself is prohibited. Additionally, providing samples of any obfuscator feature to third parties for the purpose of deobfuscation is strictly forbidden.
Licenses are strictly personal. Sharing, leasing, lending, sublicensing, or transferring a license is prohibited.
Each license is valid for one (1) individual and one (1) computer device only.
The Service may not be resold, offered, or used as a third-party service or protection.
Use of the obfuscator in virtual machines (VMs), sandboxes, emulators, cloud instances, shared systems, or any multi-user or hosted environments is strictly prohibited.
For each license, HWID reset requests are limited to a maximum of two (2) times per month.
We respect your privacy and are committed to transparency about data collection.
Rika .NET Obfuscator collects only two pieces of information: an anonymous Hardware ID (HWID) that represents your machine and your IP address. We do not collect any personal information, file contents, or any other data.
Although the obfuscation process is performed server-side, your files are immediately and permanently deleted after obfuscation is complete.
The process: Your file is uploaded → obfuscated on our server → returned to you → immediately deleted with zero trace.
We generate an anonymous hardware identifier to verify your license and ensure it is used on authorized devices only.
Your IP address is collected for the following security and operational purposes:
We do not share, sell, or distribute any collected data to third parties. All data is stored securely and used solely for the purposes stated above.